A Mutable Log
A blog by Devendra Tewari
Project maintained by tewarid Hosted on GitHub Pages — Theme by mattgraham
Information in a PCAP file with a single TCP/IP packet
If you need to create packets for your protocol so that you can test a Wireshark dissector, the following information may be useful to you. The PCAP file format is well documented in the Wireshark Wiki.
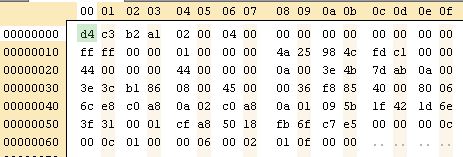
| Offset | Field description |
|---|---|
| 00 | 24-byte PCAP global header (see magic number 0xa1b2c3d4 sequence to determine how fields are to be read) |
| 18 | 16-byte packet header |
| 20 | 4-byte length of packet in file (same byte order as magic number) |
| 24 | 4-byte original length of packet (same byte order as magic number) |
| 28 | 14-byte Ethernet frame header |
| 36 | 20-byte IPv4 header |
| 38 | Total length of IP packet, includes the IP header and the TCP payload |
| 40 | 2-byte IP packet checksum |
| 4a | 20-byte TCP header |
| 4a | 2-byte source port |
| 4c | 2-byte destination port |
| 5e | Payload |
If you mess around with the payload, the fields in red are the ones you will need to adjust. The fields in blue don’t prevent Wireshark from opening the capture file correctly, but may need to be modified. You can fix the IP checksum based on the value calculated by Wireshark.